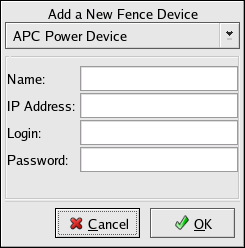
Configuring fence devices for the cluster consists of selecting one or more fence devices and specifying fence-device-dependent parameters (for example, name, IP address, login, and password).
To configure fence devices, follow these steps:
-
Click Fence Devices. At the bottom of the right frame (labeled Properties), click the Add a Fence Device button. Clicking Add a Fence Device causes the Fence Device Configuration dialog box to be displayed (refer to Figure 4.4, “Fence Device Configuration”).
-
At the Fence Device Configuration dialog box, click the drop-down box under Add a New Fence Device and select the type of fence device to configure.
-
Specify the information in the Fence Device Configuration dialog box according to the type of fence device. Refer to Appendix B, Fence Device Parameters for more information about fence device parameters.
-
Click OK.
-
Choose File => Save to save the changes to the cluster configuration.