Chapter 20. Basic Firewall Configuration
Just as a firewall in a building attempts to prevent a fire from spreading, a computer firewall attempts to prevent computer viruses from spreading to your computer and to prevent unauthorized users from accessing your computer. A firewall exists between your computer and the network. It determines which services on your computer remote users on the network can access. A properly configured firewall can greatly increase the security of your system. It is recommended that you configure a firewall for any Red Hat Enterprise Linux system with an Internet connection.
20.1. Security Level Configuration Tool
During the Firewall Configuration screen of the Red Hat Enterprise Linux installation, you were given the option to enable a basic firewall as well as allow specific devices, incoming services, and ports.
After installation, you can change this preference by using the Security Level Configuration Tool.
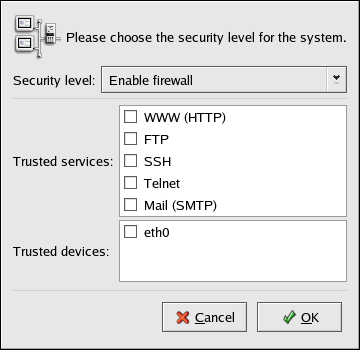
To start the application, select Main Menu Button (on the Panel) => System Settings => Security Level or type the command redhat-config-securitylevel from a shell prompt (for example, in an XTerm or a GNOME terminal).
 | Note |
|---|---|
The Security Level Configuration Tool only configures a basic firewall. If the system needs to allow or deny access to specific ports or if the system needs more complex rules, refer to the Red Hat Enterprise Linux Reference Guide for details on configuring specific iptables rules. |
Select one of the following options:
Disable firewall — Disabling the firewall provides complete access to your system and does no security checking. Security checking is the disabling of access to certain services. This should only be selected if you are running on a trusted network (not the Internet) or plan to do more firewall configuration later.

Warning If you have a firewall configured or any customized firewall rules in the /etc/sysconfig/iptables file, the file will be deleted if you select Disable firewall and click OK to save the changes.
Enable firewall — This option configures the system to reject incoming connections that are not in response to outbound requests, such as DNS replies or DHCP requests. If access to services running on this machine is needed, you can choose to allow specific services through the firewall.
If you are connecting your system to the Internet, but do not plan to run a server, this is the safest choice.
Selecting any of the Trusted devices allows access to your system for all traffic from that device; it is excluded from the firewall rules. For example, if you are running a local network, but are connected to the Internet via a PPP dialup, you can check eth0 and any traffic coming from your local network will be allowed. Selecting eth0 as trusted means all traffic over the Ethernet is allowed, but the ppp0 interface is still firewalled. To restrict traffic on an interface, leave it unchecked.
It is not recommended that you make any device that is connected to public networks, such as the Internet, a Trusted device.
Enabling options in the Trusted services list allows the specified service to pass through the firewall.
- WWW (HTTP)
The HTTP protocol is used by Apache (and by other Web servers) to serve webpages. If you plan on making your Web server publicly available, enable this option. This option is not required for viewing pages locally or for developing webpages. You must have the httpd package installed to serve webpages.
Enabling WWW (HTTP) will not open a port for HTTPS, the SSL version of HTTP.
- FTP
The FTP protocol is used to transfer files between machines on a network. If you plan on making your FTP server publicly available, enable this option. The vsftpd package must be installed for this option to be useful.
- SSH
Secure Shell (SSH) is a suite of tools for logging into and executing commands on a remote machine. To allow remote access to the machine via ssh, enable this option. The openssh-server package must be installed to access your machine remotely using SSH tools.
- Telnet
Telnet is a protocol for logging into remote machines. Telnet communications are unencrypted and provide no security from network snooping. Allowing incoming Telnet access is not recommended. To allow inbound Telnet access, you must have the telnet-server package installed.
- Mail (SMTP)
To allow incoming mail delivery through your firewall so that remote hosts can connect directly to your machine to deliver mail, enable this option. You do not need to enable this if you collect your mail from your ISP's server using POP3 or IMAP, or if you use a tool such as fetchmail. Note that an improperly configured SMTP server can allow remote machines to use your server to send spam.
Click OK to save the changed and enable or disable the firewall. If Enable firewall was selected, the options selected are translated to iptables commands and written to the /etc/sysconfig/iptables file. The iptables service is also started so that the firewall is activated immediately after saving the selected options. If Disable firewall was selected, the /etc/sysconfig/iptables file is removed, and the iptables service is stop immediately.
The options selected are also written to the /etc/sysconfig/redhat-config-securitylevel file so that the setting can be restored the next time the application is started. Do not edit this file by hand.
Even though the firewall is activated immediately, the iptables service is not configured to start automatically at boot time, refer to Section 20.2 Activating the iptables Service for details.